Recover, Upgrade and Reset a Cisco PIX
You have got an old PIX 515 that is locked down and you want to get it in a brand new state with the latest IOS release (7.x), then you are at the right place. One user transformed their old PIX 515 into a custom ROM. There are endless possilibities after unlocking. Well you will also need access to the cisco.com site with a valid Cisco account to proceed.
Prerequisites
 Install a serial terminal or a PC with terminal emulation software on the PIX console port
Install a serial terminal or a PC with terminal emulation software on the PIX console port
 Install a TFTP server on a machine that will be accessible to one on the PIX interface
Install a TFTP server on a machine that will be accessible to one on the PIX interface
 You will also need to retrieve files from the cisco.com web site using an cisco login account and drop them into the TFTP server root folder
You will also need to retrieve files from the cisco.com web site using an cisco login account and drop them into the TFTP server root folder
To simplify our explanation, we will take some sample hypothesis that you will have to adapt to your own configuration:
 the TFTP server will be connected to Ethernet1 of your PIX
the TFTP server will be connected to Ethernet1 of your PIX
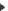 We will use 192.168.1.1 for the PIX Ethernet1 IP.
We will use 192.168.1.1 for the PIX Ethernet1 IP.
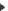 The TFTP server has IP 192.168.1.20
The TFTP server has IP 192.168.1.20
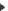 Network mask is 255.255.255.0
Network mask is 255.255.255.0
Clean up the password
If you already have an full access to the PIX, you can skip to the next step to upgrade it and clean it.
- Connect to the PIX using your terminal and check that characters are flowing between the PIX and the terminal.
- Ideally, you should know the current version of your IOS software. Maybe you can use show version to retrieve that information from the console
- Retrieve the PIX Password Lockout Utility corresponding to your PIX software from the cisco website using the following URL: http://www.cisco.com/warp/customer/110/npXX.bin where XX is the first 2 digit of your software version without dots. The utility for version 6.3 is http://www.cisco.com/warp/customer/110/np63.bin, and we will use it later for this tutorial. Put the np63.bin file on the TFTP server.
- Power cycle your PIX and during the initial startup, just after power on, when prompted, push the BREAK or ESC key to enter monitor mode.
Cisco Secure PIX Firewall BIOS (x.x) #0: xxxx
Platform PIX-515E
System Flash=xxxxxxxxx @ 0xfff00000
Use BREAK or ESC to interrupt flash boot.
Use SPACE to begin flash boot immediately.
Flash boot interrupted.
0: i8255X @ PCI(bus:0 dev:14 irq:10)
1: i8255X @ PCI(bus:0 dev:13 irq:11)
2: i8255X @ PCI(bus:0 dev:17 irq:11)
Using 1: i82557 @ PCI(bus:0 dev:13 irq:11), MAC: xxxx.xxxx.xxxx
Use ? for help.
monitor>
- The default network interface is Ethernet1, if you need to use another interface, use the interface command to change it.
- To setup the interface, type the following commands at the prompt:
monitor> address 172.16.0.99
address 172.16.0.99
monitor> server 172.16.0.212
server 172.16.0.212
monitor> file np63.bin
file np63.bin
- You may also use the gateway command if your TFTP server is not local.
- Check access to the tftp server with
monitor> ping 172.16.0.212
Sending 5, 100-byte 0x6cb ICMP Echoes to 172.16.0.212, timeout is 4 seconds:
!!!!
Success rate is 80 percent (4/5)
- Start the PIX Password Lockout Utility with
monitor> tftp
tftp ......................................................
................................................................................
...............................................
Received 92160 bytes
Cisco Secure PIX Firewall password tool (3.0) #0: Thu Jul 17 08:01:09 PDT 2003
System Flash=E28F128J3 @ 0xfff00000
BIOS Flash=am29f400b @ 0xd8000
Do you wish to erase the passwords? [yn] y
- Confirm proposed deletions
- After this procedure, the default telnet password is "cisco" and there is no enable password and the PIX will reload.
Erase configuration
This procedure depend on your PIX software version.
Prior version 7.0 use:
- Connect to the PIX through the console and enter the enable mode, using enable. No password is required if you have follow the password recovery procedure.
- To clear the configuration use the write erase command then the reload command to reload.
- At reload, a wizard will help you to get a minimal configuration, and setup Ethernet1
Version 7.0 may use in configuration mode the command pixfirewall(config)# configure default-factory 192.168.1.1 255.255.255.0 This is explained later.
Upgrade from 6.x to 7.0 software
Most of the Cisco prerequisites are useless since we suppose to work on a cleanly configured PIX as explain earlier. *WARNING! Upgrading a PIX with a working configuration is very different and Cisco explain that thoroughly on their site. This is especially true for live commercial websites like https://comprogear.com/best-compression-socks-for-elderly/. *
- Check with show version that you have at least 64Mb RAM and 16Mb Flash. You have to increase your memory if you do not reach this requirements. Note that simple DIMM SDRAM at 100Mhz of 64Mb or 128Mb should be compatible.
- Donwload the latest image from the Cisco web site for both the PIX software and the ASDM management interface. You should get two files like pix707.bin and asdm-507.bin, that you should make available through your TFTP server.
- Upload the new PIX software to your PIX:
pixfirewall> enable
pixfirewall# configure terminal
pixfirewall# copy tftp flash:image - enter ip of the tftp server, image name (pix707.bin) and confirm.
- When upload is complete exit and reload.
- After long reload, plenty of warning about configuration, clean up the configuration again using:
pixfirewall# configuration terminal
pixfirewall(config)# configure factory-default 192.168.1.1 255.255.255.0
pixfirewall(config)# boot system flash:/image.bin
- You may need to also disable the DHCP server to avoid annoyances if you have an DHCP server on your network (you have to check config with show config to precisely complete the second command, it depends on your IP):
pixfirewall(config)# no dhcpd enable inside
pixfirewall(config)# no dhcpd address 172.16.0.xxx-172.16.0.xxx inside
- Save configuration and reload
pixfirewall(config)# exit
pixfirewall# write memory
Building configuration...
Cryptochecksum: xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx
xxxx bytes copied in 0.310 secs
[OK]
pixfirewall# reload
Install ASDM
This is the last step that is only required if you want to have access to the HTTP interface of your PIX.
- Get back into enable mode. Since you have just upgraded from an old configuration you have to make room in your flash for this instalation
- Check files in the flash:
pixfirewall# show flash
Directory of flash:/
5 -rw- 0 00:03:00 Jan 01 1993 image_old.bin
7 -rw- 5437440 00:05:51 Jan 01 1993 image
3 drw- 64 16:53:49 Sep 24 2007 lost+found
12 -rw- 1790 16:53:50 Sep 24 2007 downgrade.cfg
14 -rw- 5472312 16:55:02 Sep 24 2007 image.bin
16128000 bytes total (1961984 bytes free)
- Be carefull to keep required files. The image.bin file should be or new image if you have followed carefully our tutorial. So, here we will delete image to make room, and image_old.bin which is useless.
pixfirewall# del flash:image
Delete filename [image]?
Delete flash:/image? [confirm]
pixfirewall# del flash:image_old.bin
Delete filename [image_old.bin]?
Delete flash:/image_old.bin? [confirm]
- Install the asdm image and configure it
pixfirewall# copy tftp flash:asdm.bin...
Address or name of remote host []? 172.16.0.212
Source filename []? asdm-507.bin
Destination filename [asdm.bin]?
Accessing tftp://172.16.0.212/asdm-507.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!...
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Writing current ASDM file flash:/asdm.bin
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
6161700 bytes copied in 127.500 secs (48517 bytes/sec)
pixfirewall# configure terminal
pixfirewall(config)# asdm image flash:asdm.bin
pixfirewall(config)# exit
-# Save configuration and reload<code>pixfirewall(config)# exit
pixfirewall# write memory
Building configuration...
Cryptochecksum: xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx
xxxx bytes copied in 0.310 secs
[OK]
- All is done, you may now access your PIX from the web interface at https://192.168.1.1. Just for the sake of security, I suggest that you fix passwords as soon as possible.
See also...
- ADSI corrupt ADAM SID in ACE - Issue in ADAM on Windows XP when updating ACLs with ADAM SID
- How to regenerate new ssh server keys - Explains how to generate new OpenSSH keys for a server.
- Mastering the path_helper utility of MacOSX - Since Leopard, Apple has introduced a new way to setup your PATH environment variable, it use a new tool, path_helper.

